A firewall is a critical component of network security that acts as a barrier between trusted internal networks and untrusted external networks, such as the Internet. It monitors and controls incoming and outgoing network traffic based on predetermined security rules.

Firewalls can be implemented as hardware devices, software applications, or a combination of both. They serve multiple purposes:
- Access Control: Firewalls regulate which network connections are allowed or blocked, based on configured rules.
- Threat Prevention: They protect against various external threats, including malware, viruses, and potential hacker attacks.
- Traffic Filtering: Firewalls can be configured to allow or block specific types of network traffic based on various criteria, such as:
- Source and destination IP addresses
- Port numbers
- Protocols
- Application-layer data
3. Logging and Monitoring: Many firewalls provide detailed logs of network activity, enabling security teams to detect and respond to potential threats.
4. Network Address Translation (NAT): Some firewalls perform NAT, which helps to hide internal network addresses from external networks, adding an extra layer of security.
Modern firewalls, go beyond simple packet filtering. They incorporate advanced features like deep packet inspection and application-level filtering to provide more comprehensive protection against sophisticated cyber threats.
In this article, we will focus on firewalls that operate at Layer 7 of the OSI model, also known as the application layer.
Design Flaw
When looking at how next-generation firewalls (NGFWs) work, you might notice something interesting. Let’s say the firewall rule is ‘Only Team A can use web ports (80 and 443).’ Initial port scanning with a tool like nmap might show numerous open ports, potentially misleading an observer to believe the firewall is misconfigured or ineffective. However, when trying to connect to these ports that seem open, the connection is unexpectedly cut off soon.
A specific example of this behavior can be seen in Cisco Firepower Threat Defense (FTD), which uses the Snort engine for deep packet inspection. According to Cisco documentation:
“In order for the Snort engine to determine the application, it has to inspect a few packets (usually 3-10, depending on the application decoder). Thus, a few packets are allowed through the FTD and they make it to the destination. The allowed packets are still subject to the Intrusion Policy check based on the ‘Access Policy > Advanced > Intrusion Policy used before Access Control rule is determined’ option.”
This means that even if a connection appears to start, the firewall may still block it after analyzing these initial packets. This approach allows the firewall to make more informed decisions about traffic, but it can also lead to the appearance of ‘open’ ports that aren’t actually accessible.
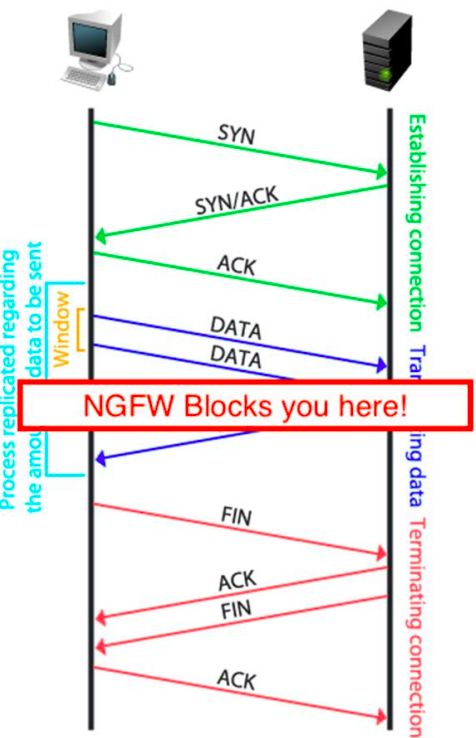
To understand how this happens, it’s helpful to know how TCP connections work.

TCP Connection Establishment (Three-Way Handshake):
1. SYN: The client sends a SYN packet with a random sequence number A.
2. SYN-ACK: The server responds with a SYN-ACK. The acknowledgment number is A + 1, and it sets its own sequence number to B.
3. ACK: The client sends an ACK with sequence number A + 1 and acknowledgment number B + 1.
From here, the application can start to communicate and send data via the session established. To close a connection, the endpoint that wants to terminate the communication initiates the connection termination:
TCP Connection Termination (Four-Way Handshake):
1. FIN: One host sends a FIN packet to start closing the connection.
2. ACK: The other host acknowledges the FIN.
3. FIN: The second host sends its own FIN when ready to close.
4. ACK: The first host sends a final ACK.
Back To Fundamentals
By now, we know that the IPS/IDS engine will initially let some packets through until it determines whether they are bad/malicious traffic or not. So, we can change the common programming practice and exploit this feature.
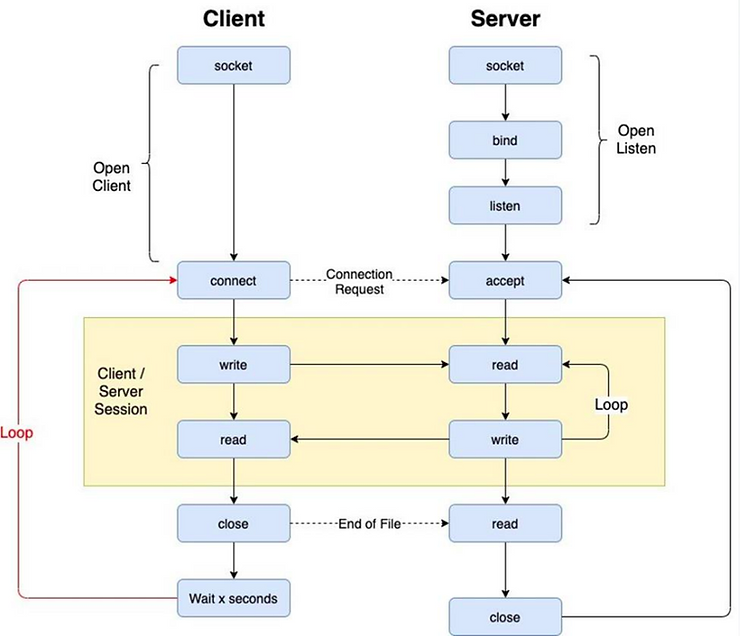
The general architecture for socket programming looks like this:

We can connect, send data, receive responses, close the socket, and repeat. This helps avoid detection by IDS/IPS systems that might otherwise block the connection. The modified algorithm looks like this:
That’s exactly what Fragtunnel does!
Fragtunnel
This Python-based TCP tunnel tool offers a unique method for circumventing next-generation firewalls:
Key Features:
- Distinct from traditional proxies or standard tunnels.
- Enables application traffic tunneling to target servers, evading NGFW detection.
Operational Mechanism:
- Data Fragmentation: Incoming application data is divided into smaller fragments.
- Multi-Session Transmission: Each fragment is sent individually through separate TCP sessions.
- Data Reassembly: Fragments are recombined at the destination to reconstruct the original data.
- Final Delivery: Reassembled data is forwarded to the intended target.
Installation
To get started, simply download the script from GitHub and run it. However, please note that for the script to function properly, setting up both a tunnel server and a tunnel client is required.
Perform the following steps on the server:
server> git clone https://github.com/efeali/fragtunnel.git
server> cd fragtunnel/
server> sudo python3 fragtunnel.py -b 127.0.0.1:80 -v
- -b, –bind: Specifies the IP address and port on which the tunnel server will listen for incoming connections.
- v, –verbose: Enables verbose mode, providing more detailed output or logging information during the execution of the tunneling application.
Actions on the client’s side:
kali> sudo python fragtunnel.py -p 1234 -t <target_IP>:80 -T <server_IP>:80 -v
- -p, –port: Specifies the port number on which the local application will listen to establish a connection.
- -t, –target: Specifies the IP address and port of the target server or service that the local application intends to connect to.
- -T, –Tunnel: Specifies the IP address and port of the tunnel server that will facilitate the connection between the local application and the target server.
Once the tunnel client is running and connected to the tunnel server, you can interact with a target as if you were directly accessing it locally on your machine.

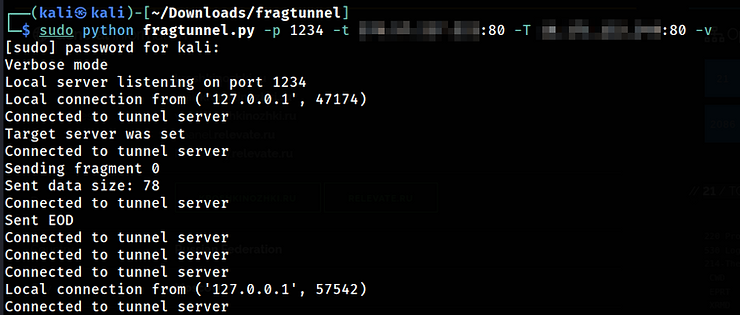
If we run tcpdump, we will notice that all communication takes place with the server, in this case AWS.

Summary
In many cases when doing reconnaissance, we notice that we can scan a server and get port information but when we try to connect to the system we are blocked by the firewall. Just a bit of knowledge of how these next-generation work can help us to get past them.
IDS/IPS engines used by most next-generation firewalls allow a few packets of data to reach the destination while they collect enough information to make a verdict on whether they should allow or block the traffic. This is a design flaw that can be exploited to give us unfettered access to the server with a tool such as fragtunnel.