Nearly all of us have used a search engine such as Google or Bing to find material on the web. These search engines crawl the entire web and index nearly every word contained on those pages and rank them. This enables us find the information we are looking for by simply typing in a few keywords (Google also has a special set of keywords to enable us to do Google hacking).

Now, imagine a search engine that instead of indexing the content of websites, indexed the banners pulled from each IP address (you can pull the banner on nearly every device by using Telnet or netcat). In other words, when we connect to an IP address, the device provides a banner identifying itself and some of its parameters.

Note the banner grab from a system running an Apache 2.2.22 web server on a Debian Linux operating system. This is the information that such a search engine could grab, parse and index for our search.
This information can be VERY useful for searching for vulnerable or unprotected devices. As nearly every device is connected to the Internet, such a search engine would enable us to find all the devices of a particular type (i.e. Cisco routers) or of a particular region (stoplights in California) and even SCADA systems. With so many new Internet of Things (IoT) devices entering the market place every day without proper security, such information would be a treasure trove for hackers.
Such a search engine does exist. It was developed by John Matherly in 2009 and it is named Shodan. You can find it at www.shodan.io as seen below.

Matherly’s crawler scans each IP address (there are 4.3B IPv4 IP addresses) and attempts to pull and collect the banner information from each device. This information in the banner usually includes the manufacturer of the device and some key parameters. It’s important to note here that Shodan indexes the data that is presented in the banner. It has no way of knowing whether the banner is accurate. Some firms that are vigilant about security actually replace these banners with fake or bogus banners to throw off Shodan or attackers. Although this is a good practice, when you start using Shodan, you will find that few actually do this.
Using Shodan
The first step in using Shodan is to register an account. You can use Shodan without registering, but the capabilities are rather limited. A basic account is free, so let’s register and try some searches
Before we get started creating our own searches, let’s try some that others have created and stored on the site. Among the most popular of these are web cams. Click on “Explore” in the top menu bar and it will open a page as seen in the screenshot below.

Now, let’s try some of the web cam searches. At the top and center of this screen you can see “Top Voted” searches. The very first is “Web Cams”. It’s important to note here that each type of web cam, generally, will have unique search parameters. Remember, we are searching by the banner information and what identifies it as a web cam is usually its unique name given by the manufacturer. The point I’m trying to make is that web cam or other searches on Shodan will likely require multiple searches to capture all of the devices, unless–in the unlikely case– that they are manufactured by one company and only have one product name.
Now with that caveat out of the way, let’s get back to searching for web cams. Click on the “Web Cam” tile.
When you click on it, you will see that Shodan generates a search phrase. This phrase is comprised of the key terms that will appear in the device’s banner that uniquely identify it. In this case that phrase is “Server SQ-WEBCAM”. This search in Shodan delivers over 7000 IP’s that meet that criteria and their corresponding devices are seen below.

We can click on any of these entries and it will take us to the Internet facing device. If we scroll down a bit to the lower part of the first page, we come to a a device in Lithuania (Lithuania is the most common residence of this particular device) as you can see below.

When we click on it, it takes us to the login screen of the web cam server. Since we know the default username and password for this particular device is “admin” and “admin” (default usernames and passwords are available all over the Internet. Just try Googling the device name and “default password” and you will find numerous entries), if the administrator left these in place without changing them, we may be able to login to their web video server.

When we try those credentials, they work! We are in!

As you can see above, we were able to access the administration panel of the web cam server with all of its controls! This system admin was definitely TOO busy to change the default credentials and now their web cam server can easily be compromised.
Webcamxp
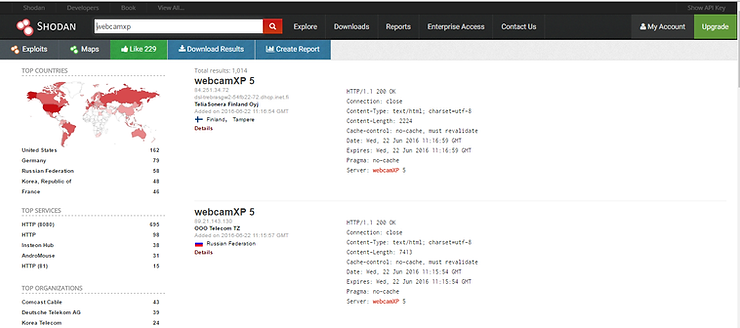
Another interesting search within the realm of web cams is “webcamxp”. These particular web cams are almost always unprotected, so that when you find one, you can simply click on the IP and begin viewing the images captured by these cams. When we put “webcamxp” into the search bar, Shodan finds over 1000 of these web cams.
Below, I have found a live image from a web cam inside a small office in Latvia. Notice the PTZ controls to the right of the camera image enabling us to zoom in or out and pan the area.

Obviously, there are hundreds of different manufacturers of web cams and you will need to know something about their banners to search for them. Usually, their banners will include the product name or the manufacturer. Try out a few.
Beyond Web Cams
The search for Internet enabled devices is almost unlimited using Shodan. As you can see below, I was able to find the login to the administration panel of a hydroelectric facility in Genoa, Italy using Shodan. Imagine what a malicious hacker could to the good people of Genoa if they could access that panel!

Shodan Search Syntax
Beside keyword search, Shodan allows us to be fairly specific in our search. We can, for instance, find devices by city, country or IP address or address range using CIDR notation. We can be so specific as to provide it with GPS coordinates, hostname, operating system and port.
Below, you can see the key terms that Shodan will accept and filter by. The syntax is simple in the format;
<keyword>:<value>
- city: find devices in a particular city
- country: find devices in a particular country
- geo: you can pass it coordinates
- hostname: find values that match the hostname
- net: search based on an IP or /x CIDR
- os: search based on operating system
- port: find particular ports that are open
- before/after: find results within a timeframe
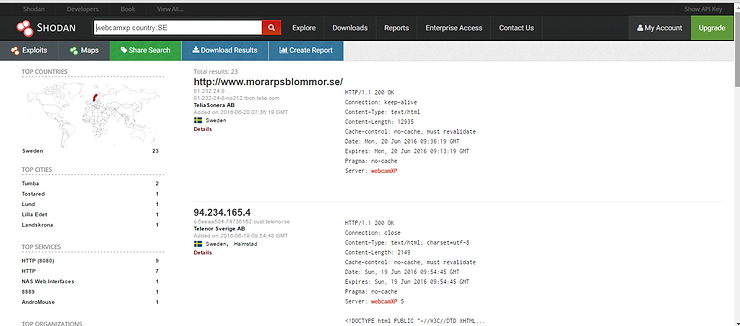
So for instance, if I wanted to find webcamxp in Sweden, I could type in the search window;
webcamxp country:SE
Or, if I want to find webcamxp in Sweden and only using port 8080, I can construct a query like;
webcamxp country:SE port:8080
Or, we could look for webcamxp in Sweden on the telia.com host by entering;
webcamxp country:SE hostname:telia
Or, we could look for those webcamxp’s in Sweden on the subnet 81.229.0.0./16 by entering;
webcamxp country:SE net:81.229.0.0/16
As you can see, the Shodan search filters enable us to be VERY specific in finding Internet connected devices.
More Shodan
In addition, Shodan has an API that enables us to connect other applications– such as recon-ng– to Shodan to use its resources and capability. This API requires that you open a premium account to access and these go from $19/month to $99/year. In future tutorials here on www.hackers-arise.com, I ‘ll show you how to find traffic signals, routers, home security systems, refrigerators (?) and just about any kind of device connected to the Internet, so keep coming back to Hackers Arise to learn the most valuable skillset of the 21st century–Hacking!
For more Shodan, check on my tutorial on using Shodan to find SCADA/ICS systems or using Shodan in conjunction with Metasploit by using AutoSploit.
SCADA Hacking: Finding SCADA Systems using Shodan
Previously, I wrote a tutorial on using Shodan–the world’s most dangerous search engine–to find unprotected web cams. As you know, Shodan simply scans the world’s IP addresses and pulls the banner and then indexes those banners. We can then search through Shodan for the parameters revealed in those banners to find IP addresses of a particular type of device.

In this tutorial, we will be looking for SCADA devices. SCADA or Supervisory Control and Data Acquisition are systems that are used for such things as electrical transmission systems, nuclear power plants, chemical plants, water treatment plants, HVAC systems, home heating, etc. All of these systems have digital controls which are all vulnerable to attack. SCADA systems are a huge concern for national defense agencies as a nation that has its SCADA systems disabled or compromised would likely have a hard time waging a successful war. This is why organizations such as the U.S. Homeland Security are SO concerned about SCADA security. Most cyber war experts expect that all future wars will have a SCADA cyber attack element.
Irongate
Just this year, the security researchers at Fire Eye found a piece of malware that specifically targets these Industrial Control Systems (ICS). That named it Irongate. It has many features similar to the infamous Stuxnet that NSA sent against the Iranian uranium-enrichment facility.

SCADA Communication Protocols
There are multiple communication protocols used in SCADA or Industrial Control Systems (ICS). Unlike Ethernet or Internet Protocols (IP), the industrial control industry uses multiple protocols, often unique to the manufacturer of the programmable logic controllers (PLC). Although there are many protocols, some of the more popular communication protocols within these systems are;
modbus port 502
dnp port 19999
dnp3 port 20000
fieldbus port 1089-91
ethernet/IP port 2222
etherCAT port 34980
profinet port 34962-64
Knowing the ports these systems operate on, may help us identify these vulnerable SCADA systems.
Modbus
Although we will look at other protocols in future tutorials, here we will focus upon finding modbus enabled SCADA systems that are Internet-facing. Modbus is one of the most common protocols in ICS and SCADA systems. Since we know that modbus uses port 502, this should not be hard to find.
Modbus is a serial communications protocol originally published by Modicon (now Schneider Electric) in 1979 for use with its programmable logic controllers (PLCs). Modbus has become a de facto standard communication protocol in SCADA/ICS systems. Modbus has become the standard because it was;
- developed with industrial applications in mind
- openly published and royalty-free
- easy to deploy and maintain
- moves raw bits or words without placing many restrictions on vendors
Modbus enables communication among many devices connected to the same network, for example a system that measures temperature and humidity and communicates the results to a computer. Modbus is often used to connect a supervisory computer with a remote terminal unit (RTU) in supervisory control and data acquisition (SCADA) systems. Many of the data types are named from its use in driving relays: a single-bit physical output is called a coil, and a single-bit physical input is called a discrete input or a contact.

Without going to additional technical details of the modbus protocol, it will suffice to say that many SCADA systems still use this popular protocol.
Shodan
Shodan enables us to search the banners and the information or parameters they reveal. Since we know that modbus runs over port 502, we could simply search Shodan for any IP’s that have that port open to the Internet. If they do, they likely are running modbus and are part of some company’s SCADA infrastructure.
Let’s open Shodan and search for IP’s with port 502 open. In the Shodan search window, type;
port:502
Note that in Shodan, we first type the parameter we are searching for (port), followed by the colon (:) and finally the value (502). When we do so, we find over 13,000 results! Although there is no guarantee that all these IP’s are running modbus, it is likely most are, as port 502 is not a popular port.
We can see the first page of results from our Shodan search below.

Note the very first result has an IP address 192.253.39.64. Beneath the IP we can see that it is based in France and is connected through the Orange (formerly France Telecom) telecommunication system. When we click on the IP, it takes us directly to the admin interface of this device using modbus.

With a little Internet research, we can that this PLC is manufactured by SAIA-Burgess, a Swiss-based company. They primarily manufacture field programmable PLC’s for the heating and cooling markets.

When we click on the login, we come to a PCD Web-Server Login. If we can login in here, we will have access to the controls of this PLC and control the temperature and energy efficiency of this facility. Although the consequences of such a breach might seem minor, Elliot Alderson (the main character in the Mr. Robot TV series) and f/society would have loved this access when they were trying to render useless E Corp’s backup tapes at the Steel Mountain facility.
After several attempted logins, I continued to receive this login page, indicating that there is no lockout of this page, making it susceptible to brute force attempts on its password.

In addition, since we know that this device is using port 502 for modbus communication, it is likely susceptible to modbus spoofing and/or DoS attack on that port (look for coming tutorials on both of those attacks on SCADA systems).
This is a good example of how SCADA systems can be identified by Shodan. Often their defenses are weak and limited and simple attacks such as brute force password cracking and DoS attacks are easily executed against them. Although this system was simple and relatively inconsequential, I have identified the GUI admin interface of nuclear power plants and hydroelectric plants via Shodan. These security engineers had better get up to speed before they become the victims of the next cyber attack.
You should be able to find other SCADA devices by searching for ports 19999, 20000, 1089-1091, 2222, 34980, and 34962-34964.
Finding SCADA Systems by PLC Name
Sometimes, you can find SCADA systems by the manufacturer or PLC name and version number number. Remember, with Shodan we are looking for the content of the systems web banner. In most cases, these systems display and banner detailing the manufacturer name, the PLC and the version. let’s look at one example.
Schneider Electric of Paris , France, is now the parent of the company that first developed the modbus protocol, Modicon. They produce a wide variety of ICS systems most of which use the modbus protocol.
Let’s begin looking for those systems by simply entering the company name “Schneider Electric” into Shodan’s search engine enclosed in double quotes. This should find all the systems that have that name in their banner.

As you can see, Shodan identified almost 3000 systems around the world with the name “Schneider Electric” in their banner. This strongly implies, of course, that the system is among the family of Schneider Electric products.
We may want to be even more specific. Schneider Electric builds an automated building system they call SAS or Schneider Automated Server. It is used to automate the heating, colling and security of high-tech buildings. If we include that additional term into our Shodan search, we should get a subset of our original search

A you can see above, our search has been narrowed to just 176 IP addresses on the planet.
In a following article, I’ll introduce to some Google dorks to find other SCADA and ICS devices, so keep coming back my rookie hackers!
In this tutorial, we will expand and extend your knowledge of the capabilities of Shodan to find outdated and vulnerable online systems.

Often times, aspiring cyber warriors assume that every computer system has the latest and greatest operating system and software and has been patched with all the most recent security patches. They believe that EVERYONE is using Windows 10, Server 2016 and the latest software release, because they and all their friends and associates are. I can assure your right now that is NOT the case. We can easily demonstrate this using Shodan.
Keep in mind that Shodan pulls banners only from Internet-connected devices. Therefore, its lists do not include all systems, but only a subset of all systems. There are far more systems in the world for a specific set of parameters than what Shodan lists.
For instance, since Microsoft first introduced in Windows XP 2001 and ceased mainstream support on April 14, 2009 and extended support on April 8 2014, you might assume that NO ONE with any information security consciousness would still be running this operating system, especially on an Internet-connected device. This would make some sense since Windows XP is riddled with security vulnerabilities longer than I can list on this page. Let’s test that assumption on Shodan.
Shodan enables us to look for the operating system hosting the IP address by using the following syntax:
os:”operating system name”
Windows XP on the Net
So, if we want to find all the systems running Windows XP connected to the Internet, we could create a filter as such
os: “windows xp”

We can see that Shodan found almost 150,000 systems connected to Internet running Windows XP. Kind of makes you salivate, doesn’t it?
Note that the second listing above is running the ancient Microsoft IIS 6.0 web server. Once again, the list of vulnerabilities for this web server is too long to list here (check CVE deatils, SecurityFocus or other vulnerability dayabase) and this company is running both Windows XP with the out-of-date Windows IIS 6.0. Windows IIS 6.0 was introduced with Windows 2003 and you probably assumed no one was still using this buggy out-of-date web server (the current version of IIS is 10.0), but you would be wrong.
Microsoft IIS 6.0 Web Server
Let’s see how many systems are still using Microsoft’s II 6.0. We can create a filter on Shodan that shows only Windows IIS 6.0 systems as such;
“Microsoft-IIS/6.0”

As you can see above, there are almost 600,000 systems running this ancient, 15 year old web server. Is anybody paying attention out there?
Windows XP AND Microsoft IIS 6.0
Furthermore, Shodan enables us to find systems running the both obsolete Windows XP and Microsoft’s buggy IIS 6.0 by using a logical AND in our filter. Shodan, like many systems, assumes a logical AND when you place two or more parameters in the filter window. So, we can find those systems running IIS 6.0 on Windows XP by creating a filter as so;
“Microsoft-IIS/6.0″ os:”Windows XP”

Shodan found over 27,000 such sites. These companies should thank their lucky stars they have not yet been hacked or maybe they have already been hacked and don’t know it. Such systems are vulnerable to almost any script-kiddie.
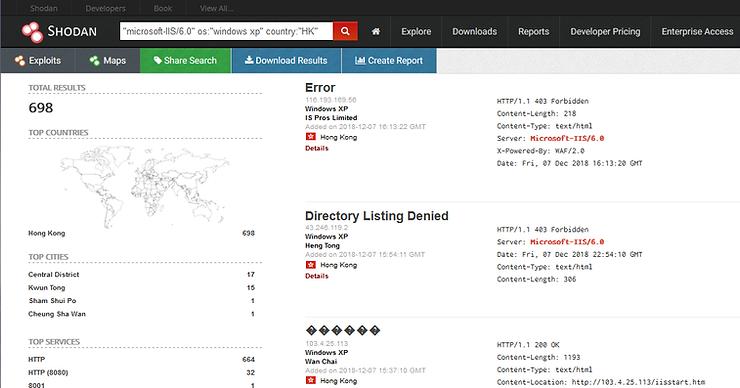
To further demonstrate the power of Shodan, we can become even more specific in our search and narrow down these systems to a specific country. To find all the IIS 6.0 systems running on Windows XP and located in Hong Kong, we could filter by;
“Microsoft-IIS/6.0″ os:”Windows XP” country:”HK”
Finding Obsolete Linux Systems
So as not to seem to be picking on Microsoft (even though everyone loves picking on Microsoft. They are such easy targets), let’s see if we can find some Internet-connected systems running an old and vulnerable version of Linux. Linux kernel version 2.6.0 was first released December 2003 and was last released in 2011 as Linux 2.6.38. This means that if we could find any systems running Linux 2.6.x they would be between 7 and 15 years old. Ancient in computer years (computer years are like dog years, 1 year is equal to 7;-)) Would anyone still be running these systems when the current kernel version is 4.19? Let’s find out!
We can find these systems by creating a filter as such;
os: “Linux 2.6”

Shodan reveals that over half million systems are running this obsolete version of Linux!
Finding Vulnerable Glassfish Servers
As one last example of old and obsolete software still being used on online systems, let’s look for the Java-based JEE server Glassfish. This software, originally developed by Sun Microsystems and now supported by Oracle, has been known to have numerous Java based vulnerabilities. In fact, Oracle announced in November 2013 that they would discontinue commercial support of this product. This product is now in release 5.0. Do you think companies would have upgraded and secured their applications with newer less vulnerable software? Maybe. Most have, but let’s see whether anyone is still running Glassfish 3.1.1, first released July 2011 and has many known vulnerabilities
Let’s create a filter looking for those negligent companies running this obsolete and vulnerable software as such;
“Glassfish Server 3.1.1”

As you can see above, over 1300 companies are still running this 7 year old software full of security vulnerabilities. This is the equivalent of negligence by the network/software engineers at these companies!
Finding the F5 Systems Vulnerable to CVE-2020-5902 using Shodan
Welcome back, my aspiring cyberwarriors!
On July 4, 2020 (US Independence Day), F5 released a security patch for their BIG-IP systems that allows the attacker to take control of the affected systems. This vulnerability is rated a 10/10 in severity and assigned CVE-2020-5902. This vulnerability is so severe that an attacker with even rudimentary skills can;
to execute arbitrary system commands, create or delete files, disable services, and/or execute arbitrary Java code. This vulnerability may result in complete system compromise. The BIG-IP system in Appliance mode is also vulnerable.
Presently, there are thousands of these unpatched systems around the world. Let’s see if we can find a few using Shodan.
Step #1: Go to Shodan.io and Login
Login to shodan.io.

Step #2: Search for Vulnerable Systems
Next, enter the following search in the Shodan search window;
http.title:BIG-IP&re:-Redirect
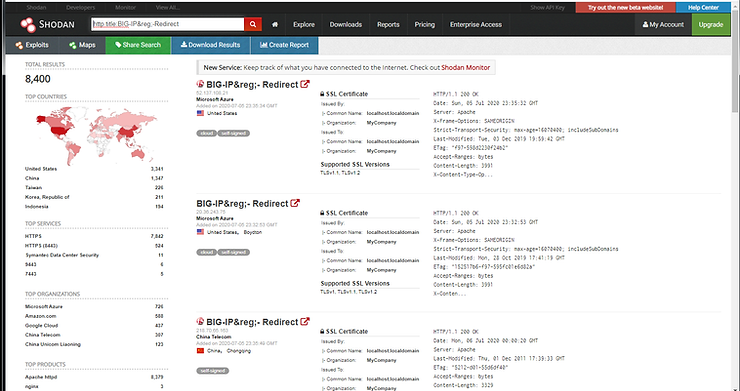
As you can see above, there are presently 8400 systems around the world vulnerable to CVE-2020-5902. Over 3300 are in the US and 1300 in China.