A firewall is one of the key security measures necessary for a secure network. Linux has a number of firewalls available to the infosec practitioner that can be crucial to securing their systems without the high cost of commercial systems. It only requires a bit of knowledge and training.
A firewall is a subsystem on a computer that blocks certain network traffic from going into or out of a computer. Firewalls can be either software or hardware based. Hardware based firewalls generally are used to protect a network and the computers on it, while a software-based firewall protects on the system hosting it.
Iptables is a flexible firewall utility built for Linux and other *nix based operating systems. It uses the command-line to setup policy chains to allow or block traffic. When someone tries to connect to your computer, iptables automatically looks for a rule to match the type of traffic. If it doesn’t find a match, it falls back to the default action.
The iptables firewall was developed by the Netfilter project and has been available as part of the Linux kernel since January 2001. As iptables has matured over the years, it has developed the functionality of many of the proprietary commercial firewalls.

Iptables Basics
iptables is made up of some basic structures known as tables, chains, and targets
Let’s look at each of these.
Tables
Tables are a iptables construct that defines categories of functionality such as packet filtering or NAT. There are four tables: FILTER, NAT, MANGLE and RAW. Filter is the default table if none other is specified. NAT is used to rewrite the source and/or destination of packets. MANGLE is used for packet alteration such as modifying the TCP header. RAW is used for configuring exemptions from connection tracking
Chains
Each table has its own built-in chains and the user can define their own chains. Chains are lists of rules within a table. For our purposes here, the most important chains are INPUT, OUTPUT and FORWARD.
INPUT
This chain is for packets destined for the local system
OUTPUT
This chain is for packets leaving the local system
FORWARD
This chain is for packets being routed through the local system
MATCH
A MATCH is where a packet meets the condition established by the rule. iptables then processes the packet according to the action in the rule.
TARGETS
iptables supports a set of targets that trigger an action when the packet meets the condition of a rule. The most important of these are ACCEPT (allow the packet to pass), DROP (drop the packet), LOG, REJECT (drop the packet and send back an error) and RETURN.
Step #1: Installing Iptables
Iptables comes installed on nearly every Linux and *nix system, but if for some reason your system doesn’t have iptables tables installed, you can download it from the repository.
kali > sudo apt install iptables

Step #2: Configuring the Default Policy
Before we begin configuring our iptables, we must first decide what will be our default policy. In other words, what should the firewall do to packets that do not match any rule.
To see the default policy on your policy chains, simply enter;
kali > sudo iptables -L

As you can see in the screenshot above, our chains are all set by default to ACCEPT. Most times, you will want your system to accept connections by default, but on very secure systems, you may want to set the default to BLOCK and then write a rule for every type of accepted connection. This is very secure but very tedious and maintenance intensive. For now, let’s leave the default policy to ACCEPT.
Step #3: iptables help
Next, let’s look at the help screen for iptables.
kali > sudo iptables -h
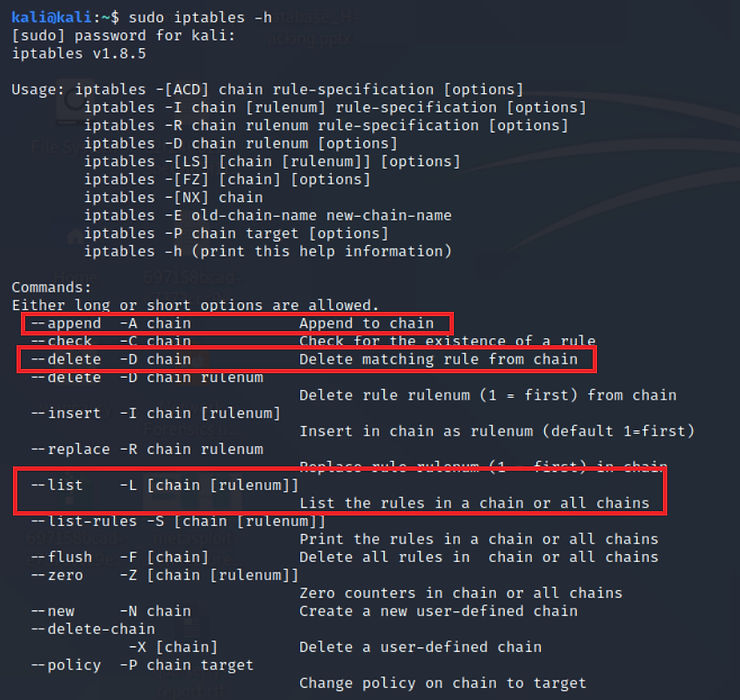
In the first of these screens, you can see the key options -A, -D and -L. They are all uppercase and they append (-A), delete(-D) and list (-L) the chain, respectively.
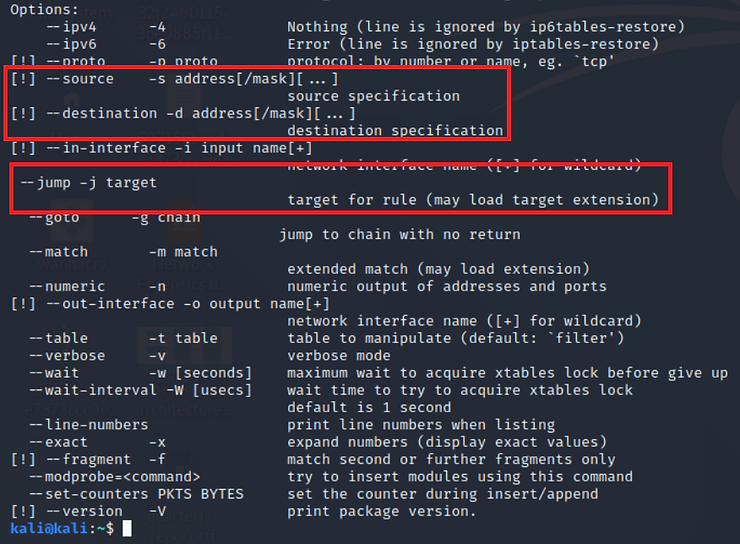
In the second screen, we can see the options -s -d and -j. These are all lowercase and indicate the source address, the destination address and the target, respectively.
Step #4: Create Some rules
Next, let’s create some rules. Let’s assume that you want to block any packets coming from IP address 192.168.1.102. To create this rule, we simply do the following;
-A this appends this rule to the chain
INPUT looks to match on packets coming to the local system
-s sets the source address of the packets
-j sets the target in this case DROP

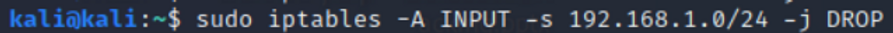
We can do the same for the entire sub-network by using CIDR notation or 192.168.1.0/24
If we want to DROP packets destined for a particular port, we can use -p option followed by the protocol (tcp) and the –dport (destination port) followed by the port (ssh).

If we wanted to accept connections to the website www.amazon.com, we could build a rule that ACCEPTs outgoing connection (OUTPUT) over the TCP protocol (-p tcp) tp amazon.com (-d amazon.com)
kali > sudo iptables -A OUTPUT -p tcp -d amazon.com -j ACCEPT

It’s important to note that iptables will do a DNS lookup only at the time of the creation of the rule. If the IP address changes, the rule will become ineffective. For this reason, it is preferable to use the IP address of the domain.
If we wanted to block access to any other websites, we could create the following two rules;
kali > sudo iptables -A OUTPUT -p tcp –dport 80 -j DROP
kali > sudo iptables -A OUTPUT -p tcp –dport 443 -j DROP

The order of these rules is critical. iptables will search the rules until it finds a match. This means that if the last 2 rules, dropping port 80 and 443, were placed before the domain rule, the user would never be able to reach amazon.com as the drop rules would match before reaching the domain rule.
So when the local system attempts to connect to amazon.com, they are blocked and the browser times out as seen below.

Finally, we can view our table by using the -L or list option

To delete a a table and start over, we can flush (-F) the table.
kali > sudo iptables -F

Now, when we list the table we can see that we have a clean slate for creating a new table.
Summary
iptables provides the Linux practitioner and cybersecurity professional a powerful and flexible firewall. With a just a bit of knowledge and practice, they can create an effective firewall rivaling the more expensive and complex commercial products costing tens of thousands of dollars.